반응형
- CloudNeta의 가시다님이 진행하시는 Terraform 101 Study에 참가하며 작성한 내용입니다.
- 스터디 교재 → 테라폼으로 시작하는 IaC
[2주차 도전과제] 1. 데이터 소스 실습
- 리전 내에서 사용 가능한 가용영역 목록 가져오기
data "aws_availability_zones" "available" {
state = "available"
}
output "available_az_names" {
value = data.aws_availability_zones.available.names
}
[2주차 도전과제] 2. 리소스 유형과 이름의 차이
- vpc와 subnet을 배포하면서 리소스 유형과 이름의 차이를 이해
- 리소스 블럭은 “<프로바이더>_<리소스 유형>” “<이름>”으로 선언
- <프로바이더>_<리소스 유형>.<이름>.<속성>으로 참조
provider "aws" {
region = "ap-northeast-2"
}
resource "aws_vpc" "hyuckang_vpc" {
cidr_block = "10.10.0.0/16"
enable_dns_support = true
enable_dns_hostnames = true
tags = {
Name = "t101-hyuckang-vpc"
}
}
resource "aws_subnet" "hyuckang_subnet_1" {
vpc_id = aws_vpc.hyuckang_vpc.id
cidr_block = "10.10.1.0/24"
availability_zone = "ap-northeast-2a"
tags = {
Name = "t101-hyuckang_subnet_1"
}
}
resource "aws_subnet" "hyuckang_subnet_2" {
vpc_id = aws_vpc.hyuckang_vpc.id
cidr_block = "10.10.2.0/24"
availability_zone = "ap-northeast-2c"
tags = {
Name = "t101-hyuckang_subnet-2"
}
}
output "aws_vpc_id" {
value = aws_vpc.hyuckang_vpc.id
}

[2주차 도전과제] 3. 입력변수를 활용한 리소스 생성
- 입력 변수를 활용하여 EC2에 Name 태그 적용
variable "name_tag" {
default = "hyuckang"
}
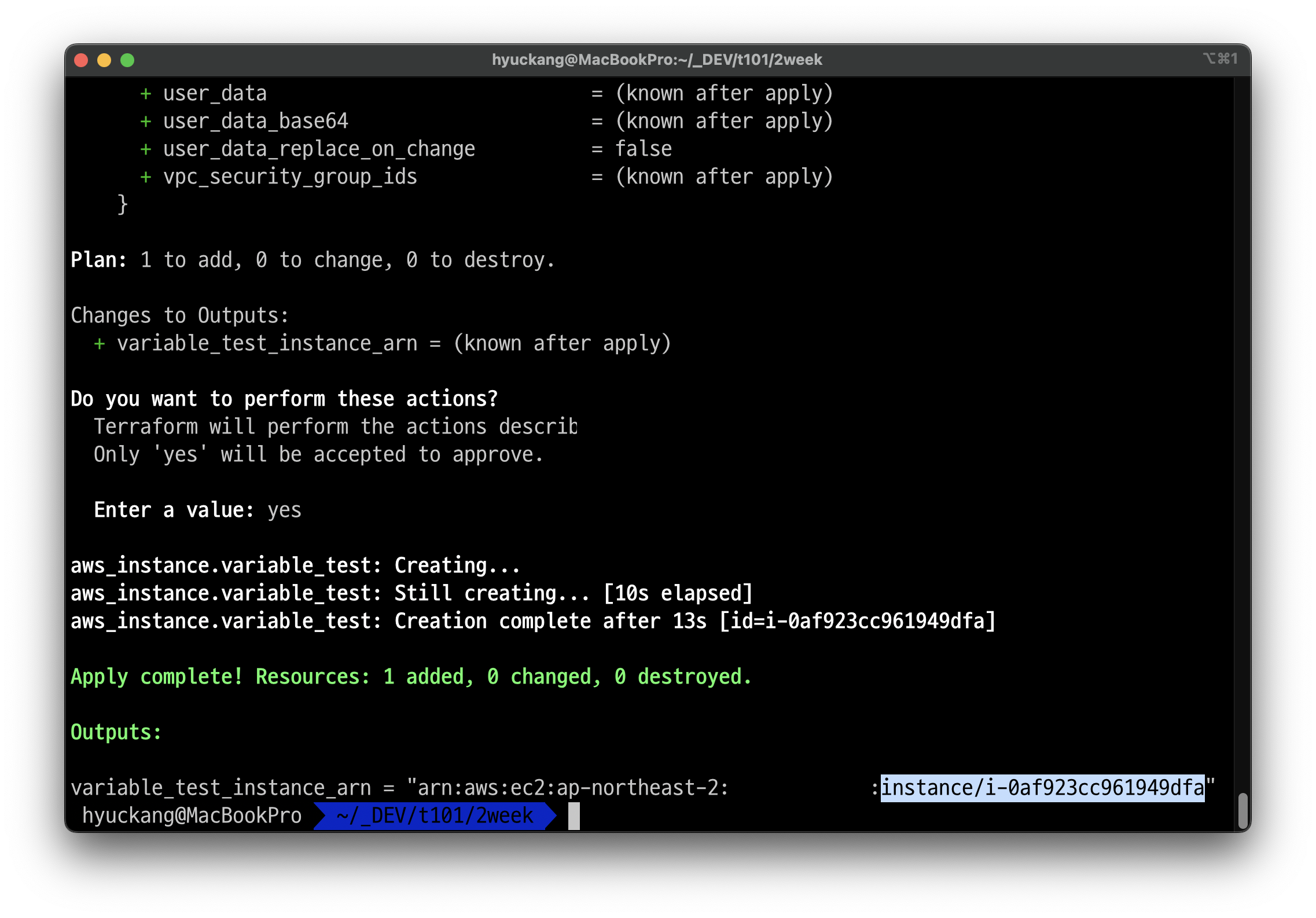
resource "aws_instance" "variable_test" {
instance_type = "t3.micro"
ami = "ami-0c9c942bd7bf113a2"
tags = {
Name = var.name_tag
}
}
output "variable_test_instance_arn" {
value = aws_instance.variable_test.arn
}

[2주차 도전과제] 4. local을 활용한 리소스 생성
- 프로바이더에 구성된 current 리전을 local에서 참조하여 region 태그 적용
# provider에 구성된 region을 확
locals {
regions = {
"ap-northeast-1" = "tokyo"
"ap-northeast-2" = "seoul"
"ap-northeast-3" = "osaka"
}
}
data "aws_region" "current" {}
resource "aws_instance" "locals_test" {
instance_type = "t3.micro"
ami = "ami-0c9c942bd7bf113a2"
tags = {
"Name" = "locals_test"
"region" = local.regions[data.aws_region.current.name]
}
}

[2주차 도전과제] 5. 반복문을 활용한 리소스 생성
- dynamic을 활용하여 sg 내에서 sg rule 반복 생성
variable "ingress_rules" {
default = [
{ protocol = "tcp", port = 80, cidr_blocks = ["0.0.0.0/0"], description = "http" },
{ protocol = "tcp", port = 443, cidr_blocks = ["0.0.0.0/0"], description = "https" },
{ protocol = "tcp", port = 22, cidr_blocks = ["0.0.0.0/0"], description = "ssh" }
]
}
resource "aws_security_group" "dynamic_test" {
name = "dynamic_test"
description = "A security group for terraform dynamic test"
dynamic "ingress" {
for_each = var.ingress_rules
content {
protocol = ingress.value.protocol
from_port = ingress.value.port
to_port = ingress.value.port
cidr_blocks = ingress.value.cidr_blocks
description = ingress.value.description
}
}
}

반응형
'📂 IaC > Terraform' 카테고리의 다른 글
| TF 101 Study 3주차 도전 과제 - 조건식, 함수, 프로비저너, 환경 변수, 프로바이더 (0) | 2023.07.23 |
|---|---|
| TF 101 Study 3주차 정리 - 조건식, 함수, 프로비저너, 환경 변수, 프로바이더 (0) | 2023.07.22 |
| TF 101 Study 2주차 정리 - data source, variable, local, output, for_each, for, dynamic (0) | 2023.07.14 |
| Terraform 101 Study - 1주차(2) 도전 과제 (0) | 2023.07.09 |
| Terraform 101 Study - 1주차(1) 내용정리 (0) | 2023.07.09 |